Key Takeaways
- Cyber threats remain common in 2023 and hence organizations must be cautious regarding cybersecurity.
- Conduct frequent security audits to find weaknesses and vulnerabilities in the system.
- Utilize technologies to monitor network traffic and look out for any suspicious trends.
- Protect sensitive data by using an encryption software system.
- Train your employees regarding cybersecurity practices and educate them to identify suspicious activities.
Online businesses need to be secure to operate; this is a fact. Why? Well, in 2023, although instances of cyber hacking have decreased, as have data leaks, online hackers are getting smarter and are working out ways to get around security procedures and barriers that businesses may have put in place.
So, if you’re setting up a business that handles online transactions in 2023, or you simply want to improve your security, how do you do this? By looking for weaknesses in your current cybersecurity systems defenses.
Do You Know?
According to the National Vulnerability Database (NVD), over 8,000 vulnerabilities were published in the first quarter of 2021.
The best ways to do just that will be explored below.
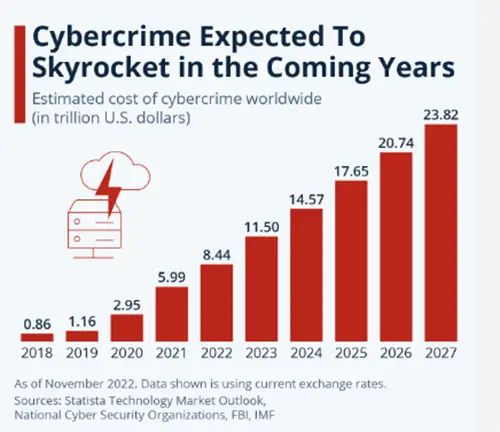
The below statistics show that by 2023, cybercrime will cost a whopping 11.5 trillion U.S. dollars. This will have a massive financial impact on the organizations, if not checked properly. Having security plans will not be enough to protect your data. Businesses require consistent auditing.
First, conduct them regularly, as well as penetration testing on your systems. This will involve running a computer simulation of a real-world cyberattack, which will be able to spot weaknesses in your defenses without the risk.
Various areas are covered under these audits like reviewing security policies, antivirus configurations, biometric data, and many more.
This will allow you to plug those holes in your security before real hackers get in, and these kinds of audits can be run and backed up regularly by GRC software after the initial audit.
Using older technologies makes you prone to cyber threats. Try experimenting with new technologies. Best of all, this software will automatically update with industry standards, so it does not require calling in teams to enhance your systems.
You are also required to also implement tools that will be able to track and analyze any incoming and outgoing traffic from your website. You should be looking for any unusual or suspicious patterns, such as unexpected data transfers and unauthorized access attempts to sensitive data.
As businesses adopt remote working and work-from-home practices, especially during the outbreak of the pandemic, to ensure the safety of employees. The need for network traffic analysis solutions has increased as a prerequisite to secure data transfer. By 2028, it is estimated that the network traffic analysis market will increase at 9.5% CAGR.
Likewise, you never know what lies hidden in your traffic until it seizes control and discloses some damaging information. This can indicate a potential bridge or vulnerability which, if spotted, entails that you need to act quickly. If you have software in place, this can be highlighted quickly, and you or another member of your team will be alerted.
This also demands analyzing the system logs and event data from your servers, your firewalls, and other sensitive infrastructure components. This is another area that will need to be looked over with a fine tooth comb, as monitoring the logs will help you to spot unusual activities or safety issues that can point to potential vulnerabilities in your security system.
You can then back these up with pieces of software or encryption systems that can protect these areas, and hopefully, during the next system log analysis, these issues won’t reappear. If they do, you’ll need to call in professional security teams to protect your online data.
You’ll need to educate your employees (or yourself if you’re a sole trader) about cybersecurity practices, as well as the importance of identifying and reporting suspicious activities.
Do You Know?
There are computer software options, like GRC-based software, that can allow your team to do this quickly, even if they’re working remotely, but as mentioned before, this will require specialized training.
You should also be actively encouraging the reporting of unusual incidents, as human error is one of the most common causes of cyber-hacking. More specifically, overlooking potential security hacks is one of the most common causes, so make sure that you and your team know what to look for.
The need of the hour is that businesses should be alert as cyber threats continue to rise in 2023. Your company can actively protect against these hazards by conducting regular audits, monitoring network traffic, checking system logs, and applying secure remote access. Following these methods will strengthen your company’s protection and guarantee a safe digital environment.