In the face of increasing dependence on cloud technology and the dynamic evolution of cyber threats, cybersecurity requires modern and effective solutions.
Businesses need to invest in effective IT security measures to protect intellectual property, sensitive data, and digital assets, and experience growth.
According to Statista, this market will be worth $538.3 billion by 2030. This emphasizes its significance for organizations to prevent digital risks and menace and ensure business safety.
Some effective measures include advanced end-point protection, employee training in preventing cyber warnings, multi-factor authentication, regular software updates, and continuous monitoring and threat intelligence.
These measures are not just defensive but lay the foundation for securing your business growth by protecting digital assets.
Businesses must deploy efficient cybersecurity solutions to ensure data security and maintain a safe online presence in light of the rise in online menace. There are several notable safety challenges. Let’s discuss some of them.
Digital security is still threatened by malware and spyware. These malicious computer programs have the capacity to infiltrate networks, take down safety guards, hold information, and disrupt operations.
Phishing attacks are still frequent. Cybercriminals are becoming increasingly inventive in deceiving new customers and employees to acquire personal and sensitive information or make them click on harmful links.
Hackers are encrypting victims’ files during ransomware ambushes and then demanding money to unlock them. Because of how devastating these assaults can be for business protection, it is vital to implement enhanced defence protocols and data backup plans.
To break in and obtain important information, social engineering attacks target human psychology. Because these assaults frequently prey on trust, firms must ensure their employees are knowledgeable about cybersecurity.
Cybercriminals commonly target zero-day vulnerabilities, which are newly identified software flaws for which there are no known fixes. To address these vulnerabilities, organisations must be watchful and proactive.
Cyberattacks are increasingly utilising artificial intelligence and machine learning. It will be harder to identify strikes using these technologies since they can be used to automate and improve attack tactics.
According to Forbes, employees are paramount for the effective implementation of cybersecurity strategy by any business. But, the unfortunate thing is that they could also be the weakest link.
For this, there should be adequate training programs or similar initiatives to give staff or team members the information and necessary abilities to combat cyber threats. The programs may include the following.
As per a recent study, only 44% of the employees receive cybersecurity training.

Training employees to spot phishing emails can greatly improve customer experience and lower their risk of falling for such cyberattacks.
To reduce the danger of credential theft, it is advisable to promote the development of robust passwords for every business account.
To ensure compliance and prevent data breaches, personnel must be trained on how to handle sensitive data and keep digital assets safe.
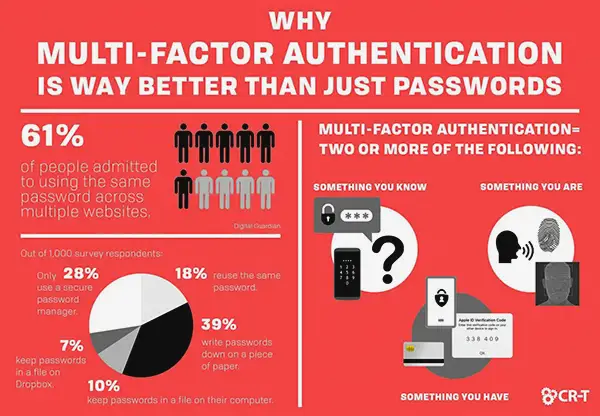
The management of cybersecurity threats by organisations requires the use of multi-factor authentication (MFA) for all firm accounts.
MFA can prevent 99.9% of cyber attacks, according to a Microsoft study. Users are required to go through several steps of authentication, including passwords and biometric data like fingerprints or facial recognition, during the login process.
Even if passwords are compromised, this gives an additional layer of security. MFA improves access control safety overall and makes it significantly more difficult for hackers to access organisation accounts or systems.
As a result, companies can successfully safeguard their customer information including financial information and other digital assets in the constantly evolving digital world.
Patches and software updates provide computers with the tools they need to defend themselves against cyber threats and bad actors.
These upgrades are pertinent for maintaining optimal functioning and safeguarding business because they act as reinforcement, strengthening the safety measures on your computer against cyber theft rather than only fixing bugs.
Subsequently, it is logical to consider update notifications as an opportunity to improve cybersecurity plans for enterprises.
Advanced endpoint security solutions such as Next-Generation Antivirus (NGAV) and Endpoint Detection and Response (EDR) have replaced traditional antivirus solutions.
These advanced technologies use machine learning and artificial intelligence to secure all endpoints of the organisational network.
These solutions prevent and detect potential hazards in real time and provide appropriate responses so that they do not materialise.
To this end, they integrate features such as antimalware, antispyware, antivirus, firewall, application control and monitoring, encryption, and access control systems. They also define restrictions and rules for users, being able to block copies, sharing, and transfers of files or information.
These technologies enable a company to enhance its protection and maintain more dynamic security systems against safety breaches, hence safeguarding digital assets and maintaining client trust as well as business reputation.
As the use of cloud and hybrid operating environments increases, Zero Trust Architectures (ZTA) are growing in popularity among firm communities.
Its main assumption is: “never trust, always verify”
According to the ZTA framework, each access to network resources must be thoroughly verified and authenticated – regardless of the source or physical location of the user.
Thinking about cybersecurity in this way allows organisations to defend themselves more effectively against cyber threats and maintain control over access to key resources.
Zero trust architecture also offers additional benefits, such as greater visibility into user and device activity. It provides organisations with detailed user and device activity logs that can be used to identify suspicious behaviour and quickly respond to potential security hazards.
Do You Know?
Zero Trust security initiatives across businesses reached 97% in 2022, up from 16% in 2019.
Continuous monitoring and threat intelligence are pivotal components of cybersecurity strategy.
Businesses can check network traffic, system logs, and other data sources continuously for any strange or suspicious activity and react accordingly. It serves as an alert guard, monitoring the outside world for prospective dangers and taking action to stop attacks and lessen harm.
On the other hand, threat intelligence allows businesses to stay ahead of cybercriminals since it helps to assess the evolving tactics or strategies of cybercriminals.
It further aids organizations to get information on emerging vulnerabilities, risks, and most recent cyberattack methods, and hence stay one step ahead of the online warnings.
In essence, continuous monitoring and threat intelligence increase the IT security posture of the firms and ensure long-term company growth and success.
Cybersecurity is not an option but a necessity for businesses that wish to thrive in the digital age. Given the constantly shifting digital environment, taking proactive measures is pivotal for securing your company’s growth, reputation, and client trust.
Implementing the vital cybersecurity measures discussed in this article will help enterprises safeguard themselves against cyber attacks and achieve long-term success.